In today’s cybersecurity landscape, threats are ever-evolving, with attackers constantly seeking vulnerabilities to exploit in software systems. To defend against these threats, organizations need to be aware of and prioritize addressing Known Exploited Vulnerabilities (KEV). Understanding KEV and the strategies to manage these vulnerabilities is crucial for protecting systems and data. In this blog, we will delve into what KEV are, their significance in cybersecurity, and how organizations can effectively mitigate these threats to enhance their security posture.
What are Known Exploited Vulnerabilities (KEV)?
Known Exploited Vulnerabilities refer to security weaknesses within software systems that have been actively exploited by threat actors in real-world attacks. Unlike theoretical vulnerabilities that might be discovered via research or simulation, KEV have been used in successful attacks, often with publicly available proof-of-concept or exploits. These vulnerabilities present a heightened risk because they are actively targeted by malicious entities.
An example of KEV is the use of vulnerabilities disclosed in software update bulletins that attackers take advantage of before organizations have had the chance to apply patches.
Significance of Addressing KEV
- Immediate Threat: KEV represent immediate security threats, as attackers are already exploiting them in the wild. Promptly addressing these vulnerabilities reduces the risk of successful exploitation.
- Prioritization: Focusing on KEV allows organizations to prioritize their vulnerability management efforts, ensuring that the most urgent threats are addressed first, efficiently utilizing resources.
- Compliance Requirements: Many regulatory requirements and industry best practices emphasize the need to patch known vulnerabilities, particularly those that have been exploited, to maintain compliance.
- Reputation and Trust: Successfully preventing exploitation of known vulnerabilities helps maintain the trust of customers and stakeholders by demonstrating a commitment to robust cybersecurity practices.
Strategies for Managing Known Exploited Vulnerabilities

- Establish a Proactive Vulnerability Management Program: A comprehensive program should include processes for regularly identifying, assessing, and remediating vulnerabilities, with a specific focus on KEV.
- Leverage Threat Intelligence Feeds: Utilize up-to-date threat intelligence feeds and vulnerability databases to stay informed about the latest exploited vulnerabilities and assess their relevance to your systems.
- Prioritize and Patch Promptly: Develop a prioritization framework that considers the severity, exploitability, and potential impact of vulnerabilities to focus efforts on mitigating KEV quickly.
- Enhance Detection and Response Capabilities: Employ tools and practices, such as security information and event management (SIEM) systems, intrusion detection systems (IDS), and automated alerting, to quickly detect and respond to any exploitation attempts.
- Conduct Regular Security Assessments: Regularly perform vulnerability assessments and penetration testing to identify unpatched KEV and other security weaknesses within your environment.
- Foster a Security-Aware Culture: Promote security awareness and training within your organization to ensure that all team members understand the importance of timely patching and adhering to secure practices.
How Kaiburr helps with KEVs?
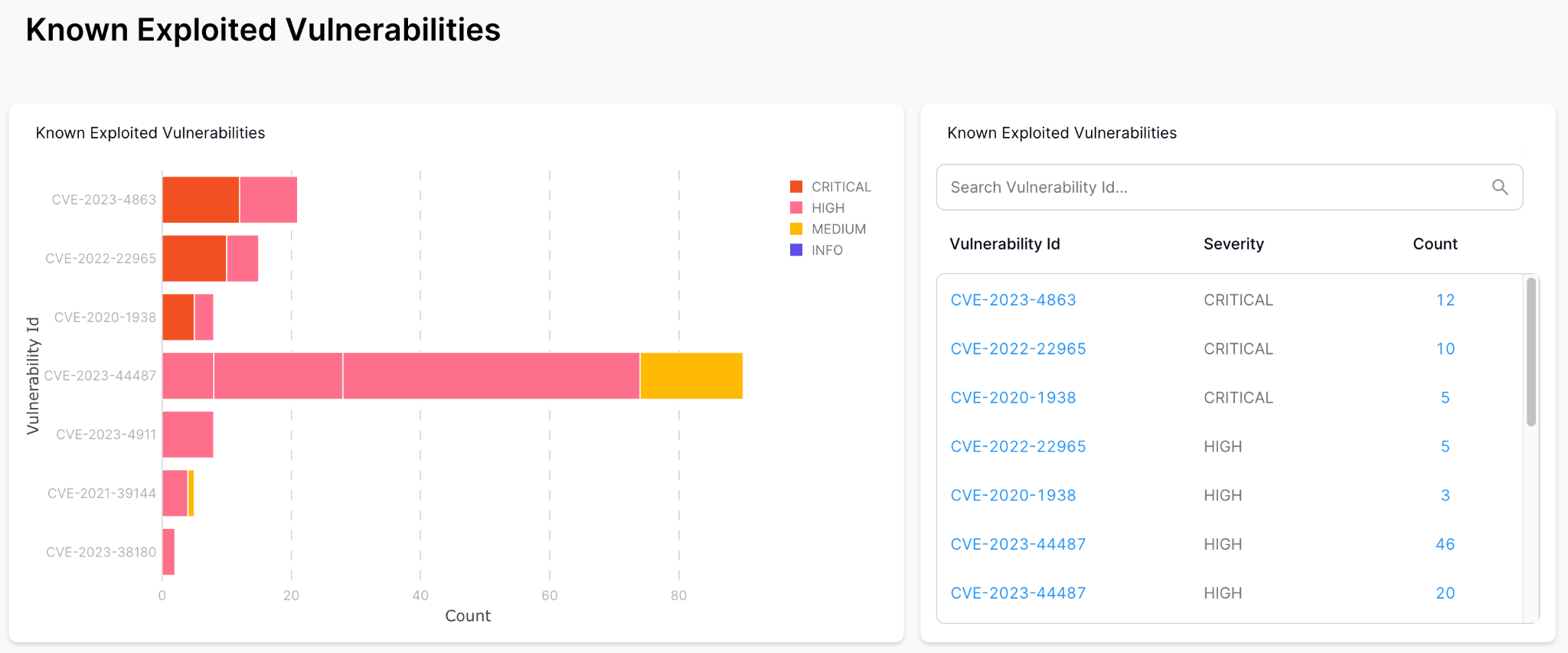
Kaiburr maps open vulnerabilities for business applications and products to Known Exploited Vulnerabilities (KEV) and aggregates them for developers and leaders to know what to prioritize and how to bundle fixes for effective use of developer bandwidth.
Here is an example of a table of KEVs and vulnerabilities to be prioritized –
Conclusion
Known Exploited Vulnerabilities (KEV) pose a significant threat to the security landscape, as they provide attackers with proven avenues for exploitation. By implementing a structured approach to identifying, prioritizing, and remediating KEV, organizations can significantly reduce their risk of compromise and safeguard their systems, data, and reputations.
A proactive and comprehensive vulnerability management program, underpinned by the latest threat intelligence and robust cybersecurity practices, is essential for dealing with KEV effectively. By focusing on these known threats, organizations not only enhance their security posture but also demonstrate a strong commitment to protecting their digital assets in a world where cyber threats continue to grow in frequency and sophistication.
Reach us at contact@kaiburr.com to master KEV metrics and empower your teams to proactively mitigate threats, strengthen cybersecurity, and safeguard your organization’s digital assets.
